Happy New Year! We couldn’t hope for a more exciting start to the year than with the groundbreaking announcement that HPE has entered into a definitive agreement to acquire Juniper. In this blog, we delve into the potential impact of this acquisition on the market, along with additional predictions for what 2024 may have in store for us:
-
The Campus Switch Market is on the Verge of a Correction in 2024
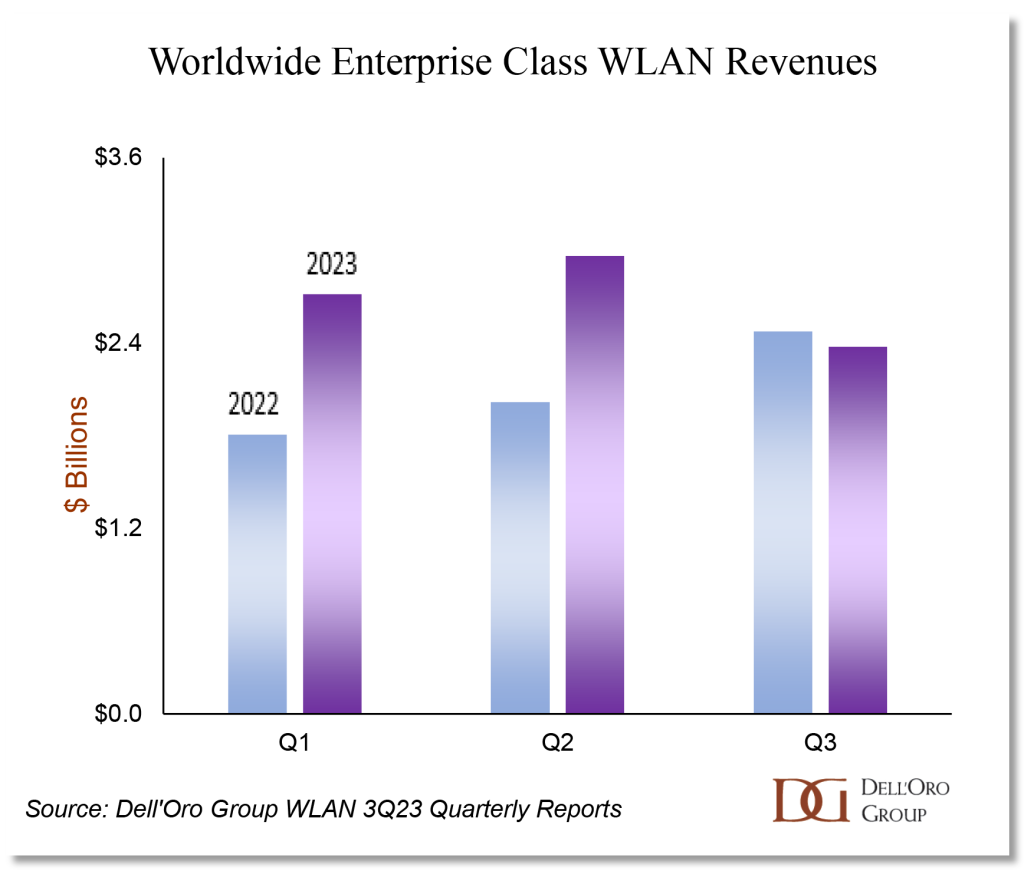
Right before the holidays, we published our 3Q23 reports which provided an overview of the market performance for the first nine months of 2023. Based on those results, the market is estimated to have grown strong double-digits in 2023, marking the third consecutive year of a very robust growth. As a reminder, the typical growth rate in the campus switch market, pre-pandemic, has been in the low-to-mid single digits. The outstanding performance in the last couple of years begs the question: where do we go from here? Based on our interviews with the vendors as well as value-added resellers (VARs) and system integrators (SIs), we believe the market is poised for a correction in 2024. We anticipate the demand in the market to slow down significantly as customers absorb and digest existing capacity. Additionally, conversations with key vendors indicate their anticipation of a return to normal backlog levels by the beginning of 2024. Once the backlog is restored to its typical state, sales performance will more accurately mirror organic market demand, eliminating the potential for backlog-driven inflation
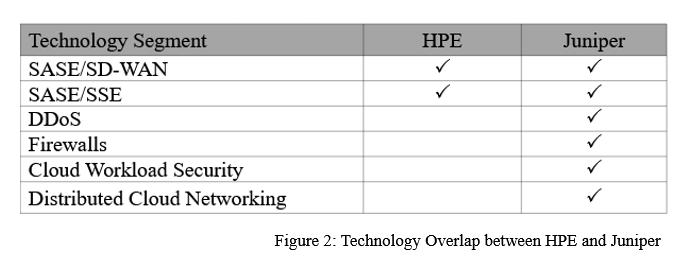
2. HPE/Juniper acquisition Will create a Tectonic Shift in the Market
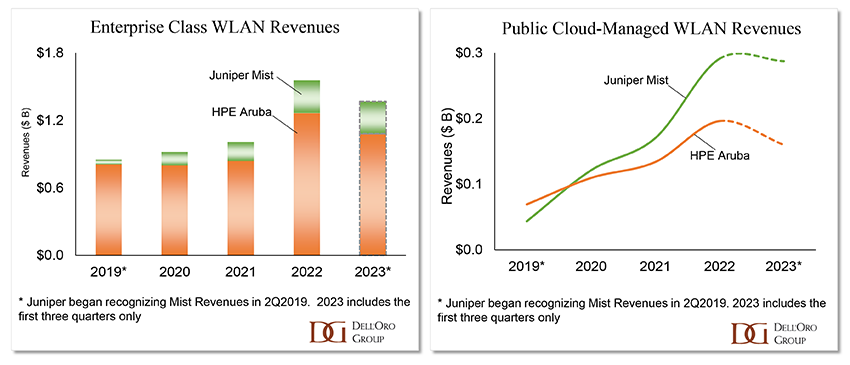
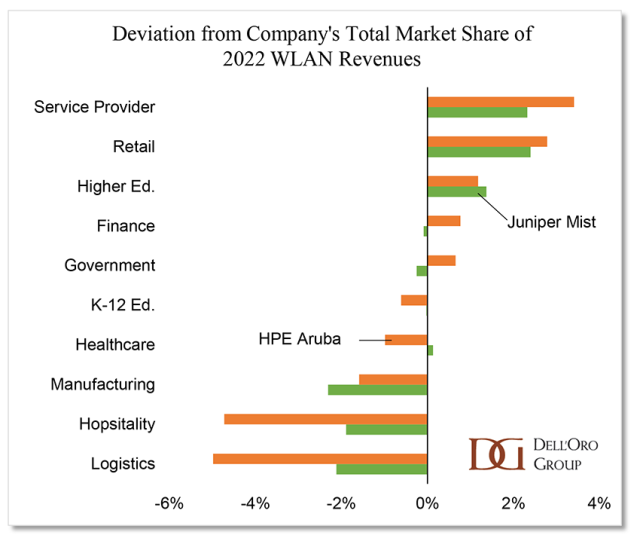
While the HPE/Juniper acquisition may not be finalized until the end of the year, we anticipate witnessing its impact on the market and competitive landscape throughout 2024. We foresee other vendors accelerating the pace of innovation and product introductions, anticipating potential synergies created by the combined HPE/Juniper entity, as explained in my HPE/Juniper blog. Additionally, we expect employees to transition between companies, fostering cross-pollination. Monitoring customer reactions will be crucial throughout the year. We believe the HPE/Juniper deal may further amplify the anticipated pause in market demand as customers will be seeking clarity on how the acquisition will impact future roadmaps.
3. AI capabilities will increasingly define the competitive landscape in the market
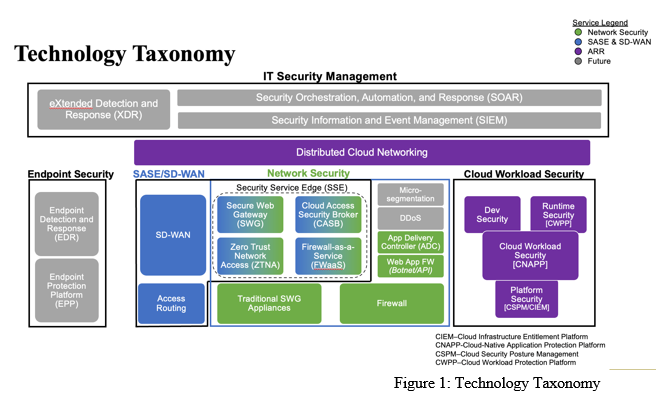
In the midst of intense competition and an expected slowdown in market demand, vendors find themselves compelled to enhance their offerings with AI capabilities. The addition of these AI capabilities brings several benefits, including product differentiation, increased demand for new use cases and applications, acceleration in product refresh cycles, and higher customer retention. However, it remains intriguing to observe vendors’ ability to effectively monetize these features. Furthermore, as customers weigh the options between on-premises and cloud-managed solutions, as well as subscription versus perpetual consumption models, we believe that AI features will play a pivotal role in influencing these choices. Customers are likely to opt for the model that allows them to benefit the most from these AI features.
For more detailed views and insights on the campus switch market, please contact us at dgsales@delloro.com