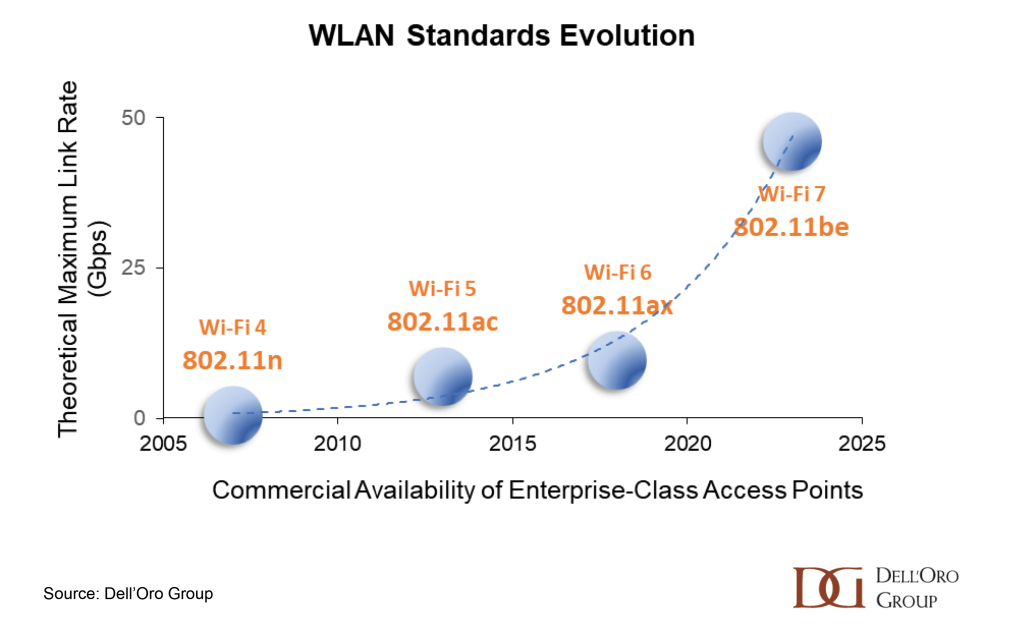
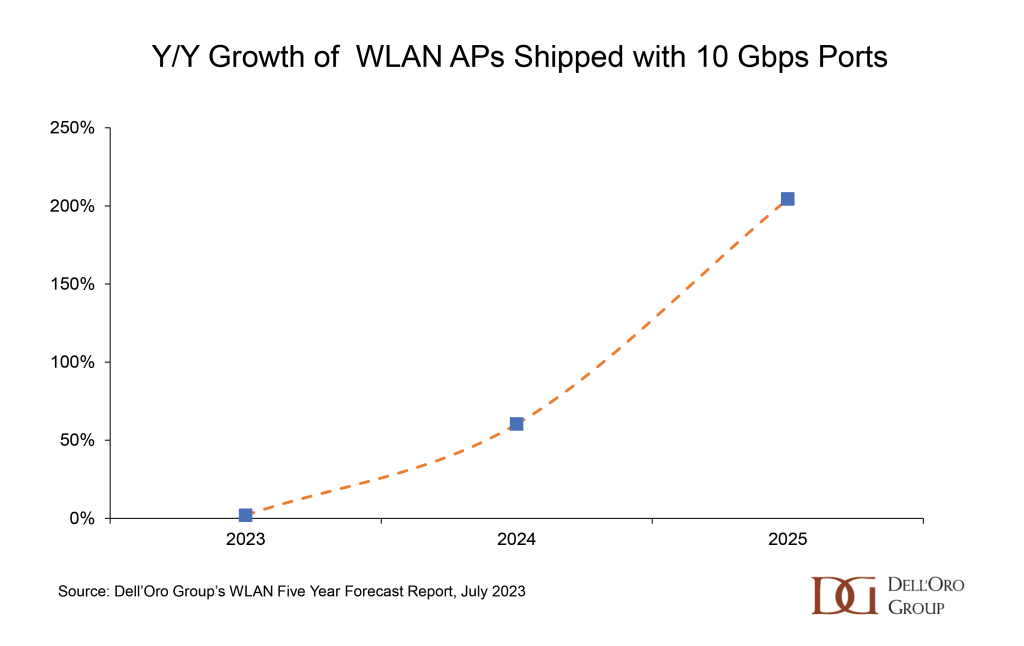
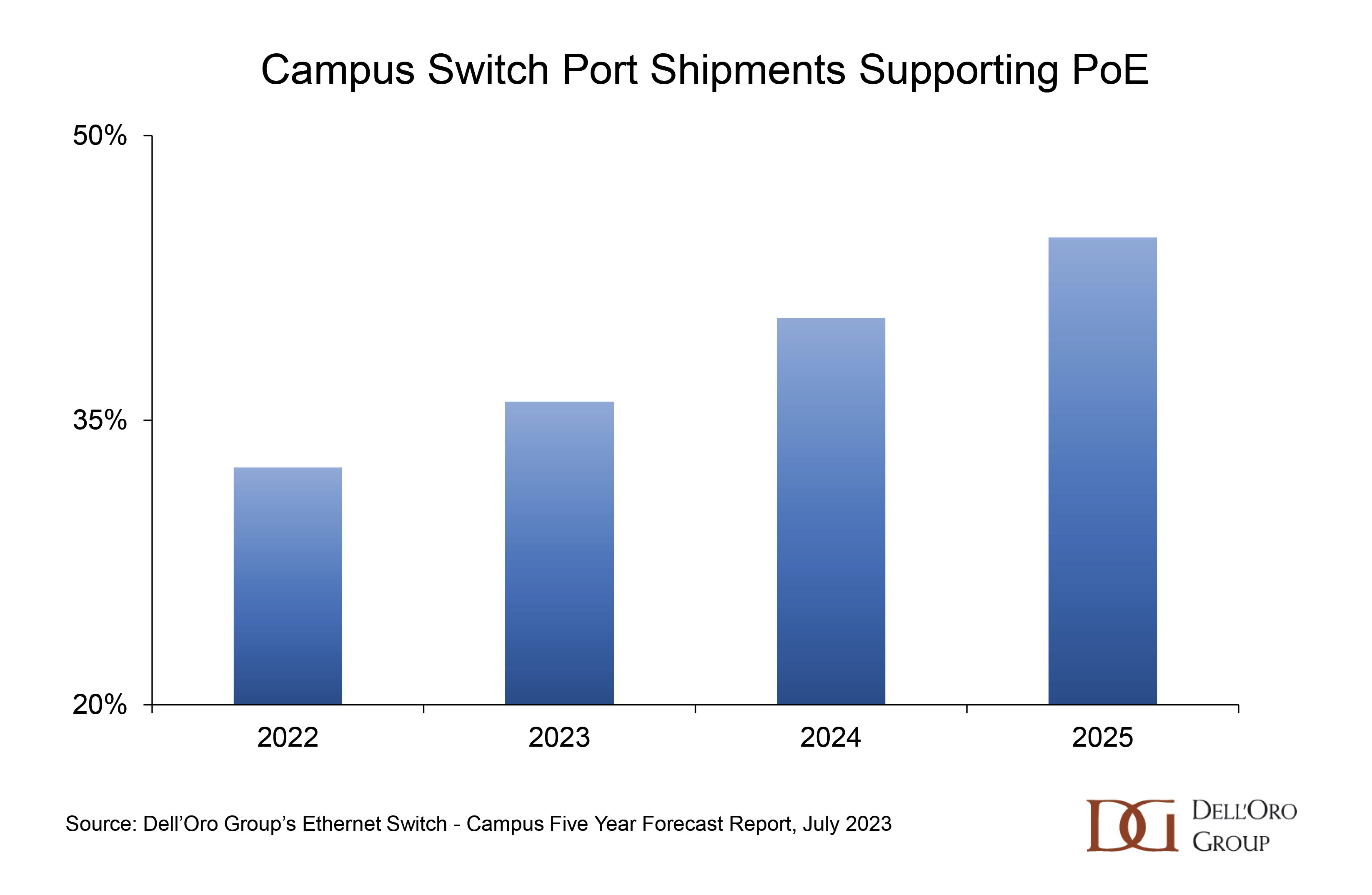
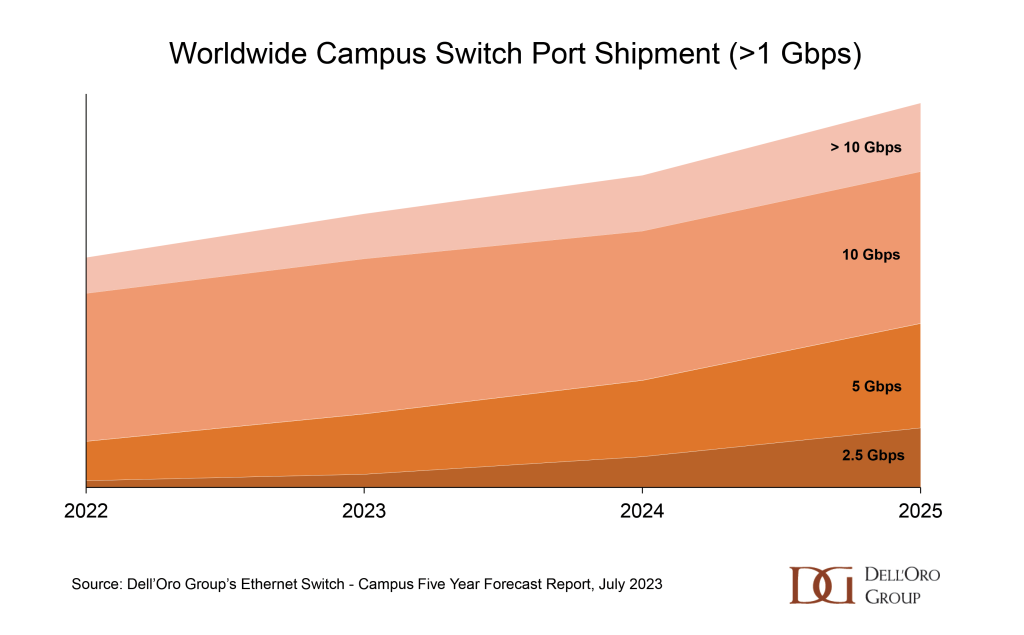
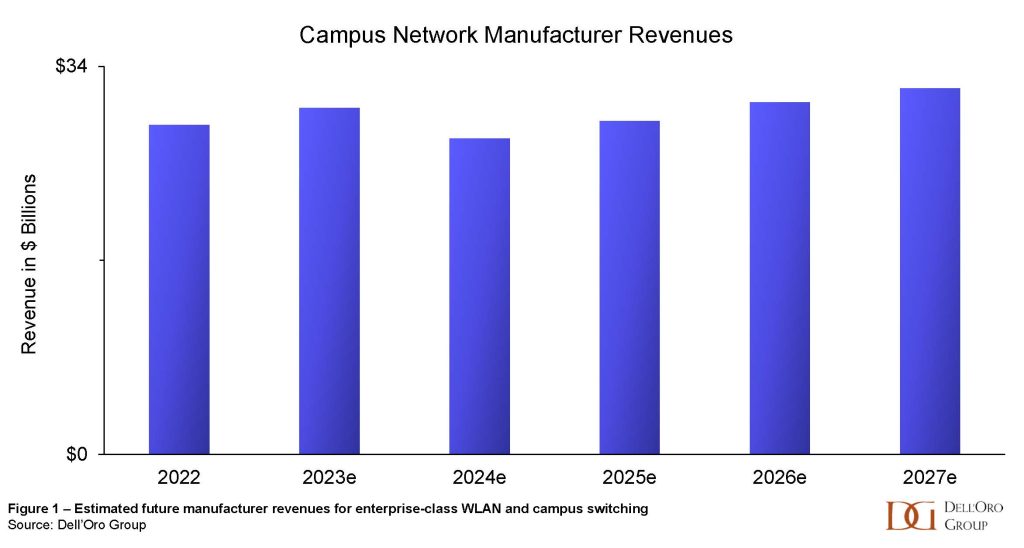
Enterprise Class WLAN sales increased by 47% Y/Y in the first half of 2023. With this meteoric acceleration in manufacturer revenues as a backdrop, industry luminaries gathered in Toronto this week at the Wi-Fi World Congress North America. Wi-Fi NOW’s CEO, Claus Hetting, hosted and facilitated the conference, peppering the speakers with questions that highlighted the innovation and thought leadership in the room. Chetan Hebbalae, formerly at Meta on TIP’s OpenWiFi project, and now VP of Products at Kyrio, summarized the essence of the event by quoting science fiction writer Arthur C Clarke: “Any sufficiently advanced technology is indistinguishable from magic.”
Advanced technology was on full display as Akoustis showed off the company’s ultra-wide bandwidth RF filters, used in HPE’s 655 access point (AP). Dave Aichele, VP of Business Development, explained that Akoustis’s mastery of material science allowed the Wi-Fi 6E AP to make full use of the new 6 GHz band, one of the few APs on the market to do so. Qorvo referenced the increased power consumption of triband APs, pointing to the power conservation of their Front End Module (FEM), and the increased competition in the FEM market keeping them on their toes.
At their booth, VVDN Technologies displayed a Wi-Fi 7 AP produced from their cutting-edge reference design. The enterprise market is seeing early product announcements in the new 802.11be (Wi-Fi 7) protocol, with H3C already selling a flagship product in China and EnGenius promising an AP in November.
Malcolm Smith of Cisco’s CTO Advisor group described how TSN (Time Sensitive Networking) with scheduling in Wi-Fi 6 and 7 could lead to bounded latency for applications such as VR. Hyper directional antennas were evangelized by Bill Anderson, AmpThink’s founder, as a game changer in stadium deployments, allowing installations at a quarter of the cost of under-seat APs. Bart Giordano, President of Ruckus at CommScope focused on the technology that has been front of mind for IT leaders since the advent of Chat GPT; explaining that the drastic reduction in the cost to train AI models will revolutionize not just enterprise WLAN, but all jobs in all domains.
The advanced science turned to the magic that Arthur C. Clarke predicted, as speakers and panelists shifted to discuss use cases and end-user experience. Elizabeth Parks, President of Parks Associates, kicked off the second day of the conference by promising that the 4th industrial revolution would be all about services and pointing to the enormous Wi-Fi opportunity in the MDU market. Only between 1 and 2% of MDU homes have access to a managed Wi-Fi service. Robert Grosz, President of WorldVue, urged conference attendees to focus on the needs of MDU property owners by emphasizing Wi-Fi as a capital asset with revenue potential, instead of just an expense.
There were plenty of other Wi-Fi use cases discussed, both practical and entertaining.
Bahador Amiri, Senior Director of Wireless Engineering at Cisco, explained that a combination of different location technologies: GPS, Wi-Fi FTM (Fine Timing Measurement or 802.11mc), and 802.11az, among others, enables asset tracking, indoor navigation, and smart workspaces. He then took the audience on a cruise ship journey, with room doors that unlocked automatically, guests that were prevented from enjoying the amenities until they had watched the safety video, and a drinks service that delivered your order wherever you were on the ship – with all of these use cases relying on Wi-Fi location services.
Keeping the focus on user experience, Michael Penney, SVP of Engineering at American Bandwidth, promised to turn Wi-Fi APs into mini cell towers, using Passpoint and OpenRoaming to transparently move end users between cell and Wi-Fi service – solving the problems related to poor cell coverage indoors.
Amidst the speakers’ presentations and panels, some contentious questions were addressed, answered, or debated during the conference.
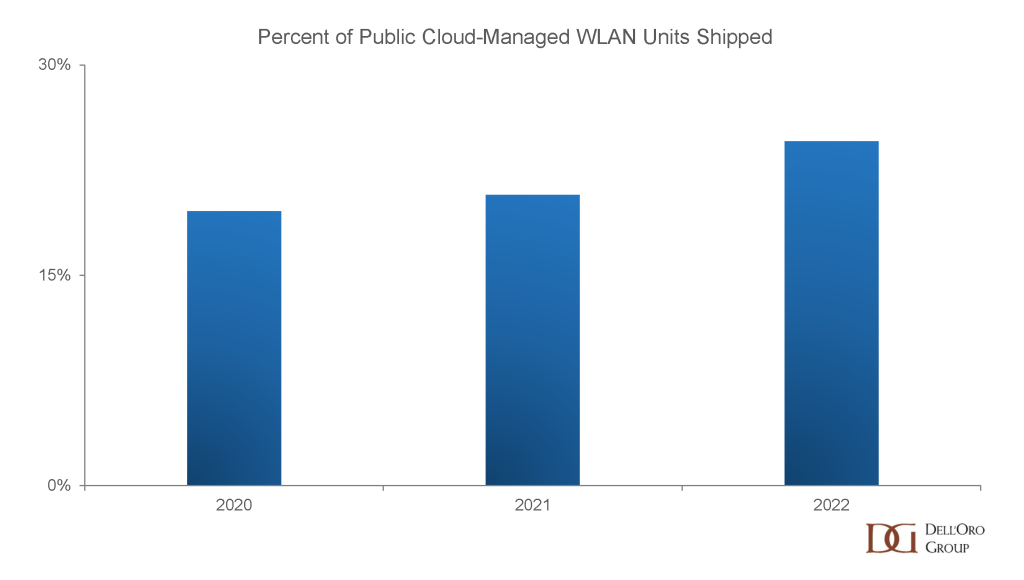
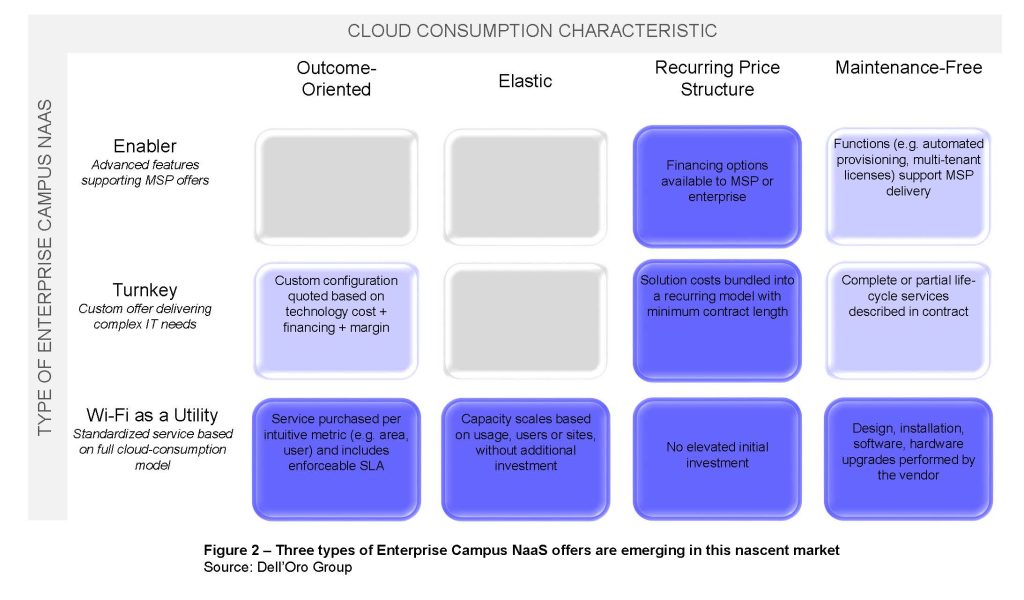
Will Campus Network As A Service expand Wi-Fi’s addressable market? There was a divergence of opinion on whether Campus NaaS was an innovative architecture or a new business model. Bob Friday, CTO and Co-Founder of Juniper’s Mist, pointed to the foundational role that AI operations played in automating Wi-Fi management. Nile’s impressive demo underlined the service’s potential. Dell’Oro Group has quantified the size of this market and its accretive potential in an Advanced Research Report entitled Campus NaaS and Public Cloud Managed LAN.
Will private 5G take market share from Wi-Fi? AmpThink’s Bill Anderson presented a fascinating analysis of two stadium deployments, one with Wi-Fi and one with cellular technology. The Wi-Fi installation was 105 times less expensive than the private cellular deployment, dropping the price per Tb from $3.9 M to $0.192 M. With its Zero Effort Networking (ZEN), American Bandwidth’s Michael Penney decried the onus of having to prove to a carrier that indoor coverage is bad, with a call to focus on user experience instead. Says Penney: indoors, Wi-Fi is the clear winner.
Is there an advantage to disaggregating Wi-Fi? OpenWiFi was front and center in a panel discussion with representatives from several companies, along with the Telecom Infra Project (TIP), demonstrating the breadth of the ecosystem. Tony Stramandinoli, VP of sales at Edgecore, explained that his company’s focus on AP hardware, and using OpenWiFi software, has enabled faster innovation. Robert Grosz of WorldVue, who deploys networks with Ruckus, Aruba, Meraki, and Cambium, has also deployed OpenWiFi solutions. He explained that after a family moves out of an apartment in an MDU, the cleaning crew can rip out or paint over the AP accidentally. For this use case, disaggregating the hardware from the software is most beneficial! Opening up the interface between the controller and the AP enables redundancy of hardware suppliers. C3Spectra and NetExperience are two companies that offer OpenWiFi compliant controllers. An SDK interface encourages innovation at the application level, highlighted by GoZone and Spectra who develop compatible application suites. Bernard Herscovici, CEO of NetExperience, referenced Purchase Orders for 5 Million Open Wi-Fi APs.
The buzz of the Wi-Fi Now Toronto event was palpable. During an evening of fancy cocktails, attendees lined up to get a signed copy of Greg Ennis’s book, Beyond Everywhere: How Wi-Fi Became the World’s Most Beloved Technology. Bart Giordano highlighted the depth of experience in attendance as he quipped that despite being around since 802.11g, he didn’t even merit a footnote in Greg’s book. With a Wi-Fi ecosystem this deep and broad, it’s no wonder it can spin science into magic.