Dell’Oro Group published an update to its Campus switch market five-year forecast report. The report shows that the campus switch market is expected to be profoundly impacted by the COVID19- pandemic and to decline at 1% CAGR from 2019 to 2024, compared to our prior January forecast of + 3% CAGR.
 Analysis of market performance during the prior two recessions was a fundamental part of our forecast process, as we assessed the impact of the COVID-19 pandemic. However, it is very important to recognize how this pandemic-induced recession may differ from the prior two recessions, not only at a macro level but also from a technology perspective. COVID-19 will bring many changes to our lives and will impact the adoption of technology in different ways. Some of these changes may be short-term, but we believe a number of them will remain with us for the long term. In the report, we detail our view on the potential impact of the COVID-19 pandemic on the market, in terms of both upside and downside. We also explain how and why this recession may differ from the prior two recessions. Our view is the result of numerous interviews over the last three to four months with end-users, system integrators, VARs, and manufacturers. Below are some highlights:
Analysis of market performance during the prior two recessions was a fundamental part of our forecast process, as we assessed the impact of the COVID-19 pandemic. However, it is very important to recognize how this pandemic-induced recession may differ from the prior two recessions, not only at a macro level but also from a technology perspective. COVID-19 will bring many changes to our lives and will impact the adoption of technology in different ways. Some of these changes may be short-term, but we believe a number of them will remain with us for the long term. In the report, we detail our view on the potential impact of the COVID-19 pandemic on the market, in terms of both upside and downside. We also explain how and why this recession may differ from the prior two recessions. Our view is the result of numerous interviews over the last three to four months with end-users, system integrators, VARs, and manufacturers. Below are some highlights:
Downside Impact from the COVID-19 Pandemic
- Although GDP outlooks are reflecting anticipation of a rebound in 2021, we expect the actual rebound in campus switch revenue to lag behind GDP recovery. This is the result of high exposure to verticals that are heavily impacted by the pandemic and may take years to recover (such as Healthcare, Higher Education, Hospitality, Logistics, Retail).
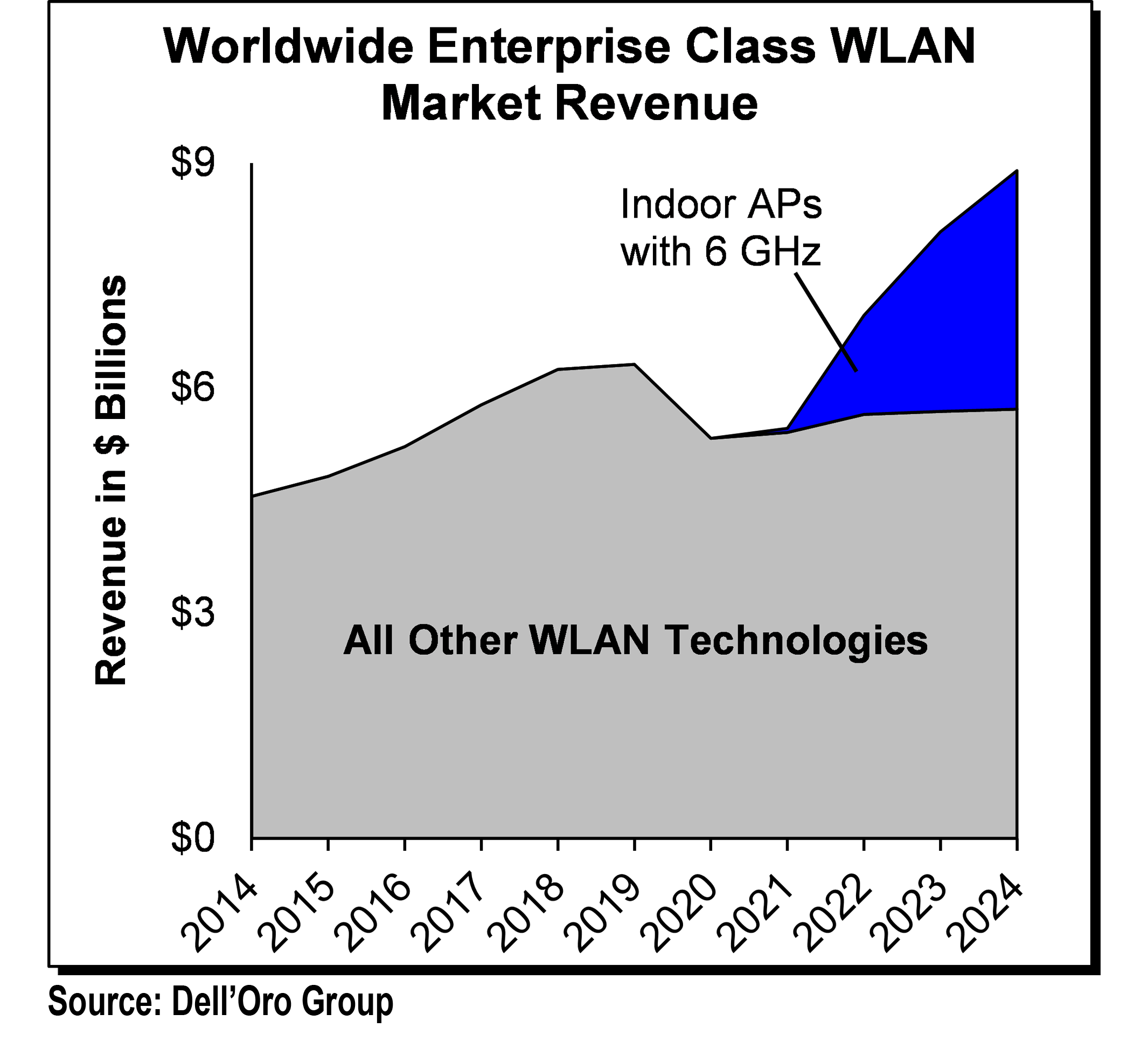
- Our interviews revealed consistent expectations among end-users, distributors, system integrators, and vendors that the portion of the remote workforce will increase following COVID19. However, it is still anyone’s guess as to what the degree will be and what the new normal will look like. Our models assume a 20% to 45% increase in the portion of remote workforce post-COVID.
- A more distributed workforce, working remotely either from home or from smaller distributed office spaces, will negatively impact the number as well as the type of switch ports needed in those campuses.
- Wireless LAN will become more favorable for user connectivity than wired Ethernet, as it supports features and services that help businesses comply with re-opening guidelines such as contact tracing, people counting, and other location-based services.
Upside Impact from the COVID-19 Pandemic
- The digital transformation is accelerating as businesses try to adapt and evolve. This, in turn, will expedite the pace of the campus switch refresh cycle. Automation, security, visibility, and analytics/intelligence are several added functionalities that IT managers need for the new digital era. We expect campus switch vendors to try to monetize those features, which may boost market average selling prices (ASPs) and help the market recover faster than currently projected.
- We forecast the higher-priced PoE ports to comprise about a third of the total campus switch ports by 2024. The increased portion of IoT devices connected to the network will drive an increased portion of the PoE ports.
- Adoption of subscription-based consumption models will become a theme during and after the pandemic. The conversion from Capex to Opex makes it much easier for companies to scale their costs down or up, according to the demand.
If you need to access the full report to obtain revenue, units, pricing, relevant segmentation including regions and vertical markets, etc., please contact us at dgsales@delloro.com
About the Report
The Dell’Oro Group Ethernet Switch – Campus 5-Year Forecast Report offers a complete overview of Ethernet switches built and optimized for deployment outside the data center, for the purpose of connecting users and things to the Local Area Networks. The report contains tables covering manufacturers’ revenue, average selling prices, and port/unit shipments by speed (Fast Ethernet, Gigabit Ethernet, 2.5 Gigabit Ethernet, 5.0 Gigabit Ethernet, 25 Gigabit Ethernet, 10 Gigabit Ethernet, 40 Gigabit Ethernet, 50 Gigabit Ethernet, 100 Gigabit Ethernet) plus regional breakouts.
 COVID-19 Near-Term Impact on WLAN Market
COVID-19 Near-Term Impact on WLAN Market

