Recently, the U.S. Department of Energy (DOE) announced $40 million in funding to accelerate innovation in data center thermal management technologies intended to help reduce carbon emissions. The funding was awarded to 15 projects, ranging in value from $1.2 to $5 Million, to universities, labs, and enterprises in the data center and aerospace industries. It will likely take 1 to 3 years for these projects to start impacting the data center industry, but following the money can provide an early indication on the potential direction of future data center thermal management technologies.
Before we assess what we can learn from the selected projects, it’s important to understand why the DOE is investing in the development of next-generation data center thermal management. It’s simple –Thermal management can consume up to 40% of a data centers’ overall energy use, second most to compute. This energy is consumed in the process of capturing the heat generated by the IT infrastructure and rejecting it into the atmosphere. The data center industry has been optimizing today’s air-based thermal management infrastructure, but with processor TDPs rising (think CPUs and GPUs generating more heat), liquid is likely required to achieve the performance and efficiency standards desired by data center operators and regulators in the near future. The type of liquid and how it is applied to thermal management has divided the data center industry on the best path forward. The COOLERCHIPS program provides a unique lens into the developments happening behind the scenes that may impact the direction of future liquid cooling technologies.
To assess the impact of the COOLERCHIPS project awards, each of the 15 projects was segmented by the type of thermal management technology and the heat capture medium. The projects were placed into the following categories (Not all projects could be applied to both segments):
- Funding by Technology (n=14)
-
- Direct Liquid Cooling: A cold plate attached to a CPU with a CDU managing the secondary fluid loop.
- Immersion Cooling: A server immersed in fluid within a tank or chassis.
- Software: Software tools used to design, model, and evaluate different data center thermal management technologies.
-
- Funding by Heat Capture Medium (n=10)
-
- Single-phase: A fluid that always remains a liquid in the heat capture and transfer process of data center liquid cooling.
- Two-phase: A fluid that boils during the heat capture process to produce a vapor that transfers the heat to a heat exchanger, where it condenses back into a fluid.
- Hybrid: Combined use of a single-phase or two-phase fluid and air to capture and transfer heat in the thermal management process.
-
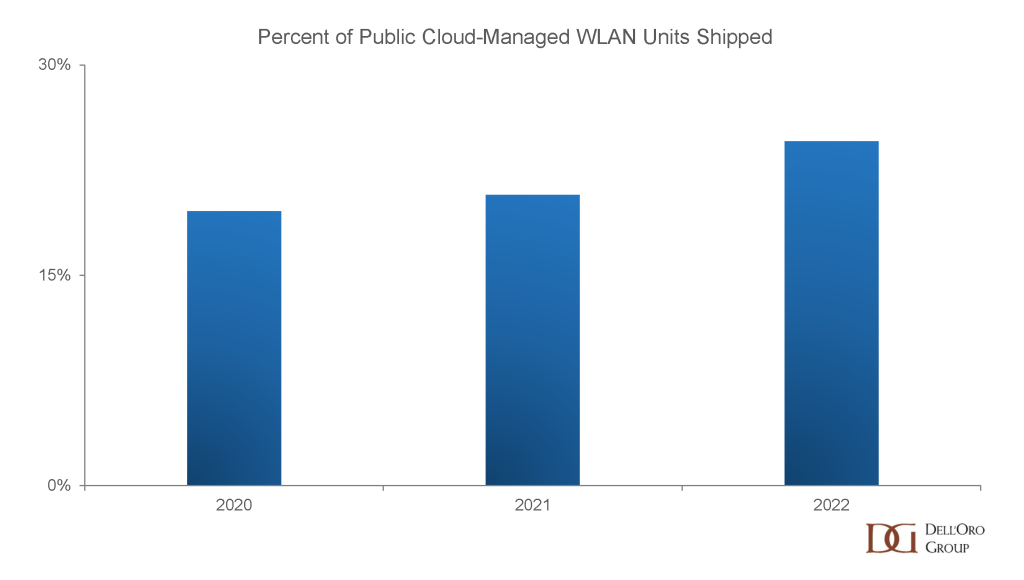
The results for funding by technology showed that direct liquid cooling accounted for 73% of awarded funds, immersion cooling 14%, and software 13%. This isn’t a particular surprise, given that direct liquid cooling is more mature than Immersion cooling in the data center industry, primarily due to the use of direct liquid cooling in high-performance computing. Additionally, the planning, design and operational changes in implementing immersion cooling have proved to be a bigger hurdle for some end-users than originally anticipated. Despite only receiving 14% of the awarded funds, there is still significant maturation occurring with immersion cooling as the installed base grows among a variety of end users. Lastly, software rounded out the projects with 13% of the awarded funds. This was a welcome addition, as software plays a critical role in thermal management design and evaluation when comparing the use of different thermal management technologies in different scenarios. Environmental factors such as temperature and humidity, computational workloads, and prioritization of sustainability can all influence which technology choice is best. Software must be utilized to align an end users’ priorities with the technology best suited to reach those goals.
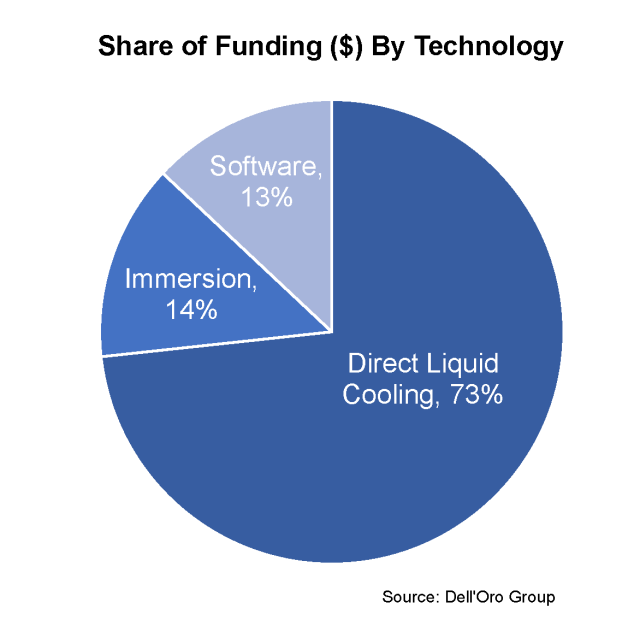
The results for funding by heat capture medium showed that two-phase solutions accounted for 48% of the awarded funds, hybrid solutions 38%, and single-phase solutions 14%. It was surprising to see two-phase solutions garner the most funding since the significant majority of data center liquid cooling today is single-phase solutions. Between 3M announcing their exit of PFAS manufacturing by 2025 and evolving European F-Gas regulations, certain manufactured fluids have been under pressure. But that may be the very reason two-phase solutions were awarded such funding – They may a play critical role in thermal management as CPU and GPU roadmaps reach and surpass 500 watt TDPs in the coming years. Inversely, it’s possible that the level of maturity in single-phase solutions is what limited the awards to only 14% of funding. Furthermore, single-phase solutions aren’t always a 100% heat capture solution, so it makes sense that hybrid solutions that bring air and liquid technologies together that do capture 100% of the heat, received more funding. Afterall, end users are increasingly interested in holistic solutions when it comes to the never-ending cycle of deploying more computing power.
Based on these results conclude data center thermal management is headed towards two-phase direct liquid cooling solutions in the medium to long term. However, it’s important to remember the maturity that is already emerging in single-phase liquid cooling solutions. This maturity is what has driven the data center liquid cooling market to account for $329 million in 2022, which is forecast to reach $1.7 billion by 2027. The liquid cooling technology and fluids will most certainly evolve over the coming years, with investments from the DOE, among many others, helping shape that direction. But most importantly, the COOLERCHIPS project awards aren’t about closing doors to solutions that already exist, but opening doors to new technologies to give us more choices for efficient, reliable and sustainable thermal management solutions in the future.