Huawei recently held its annual analyst event, HAS 2022. While we were not able to attend in person, we participated in various online events. Below we will discuss some of the RAN-related highlights when it comes to expectations for 2022, 5.5 G, 5G B2B, green sites, DIS, and Sub-3 GHz.
Challenges in 2022
Taking into consideration that the US government started banning Huawei from acquiring US components back in May 2020, Huawei has done a remarkable job supporting its 4G and 5G customers, contributing to the stable revenue trends for the broader carrier group over the past couple of years.
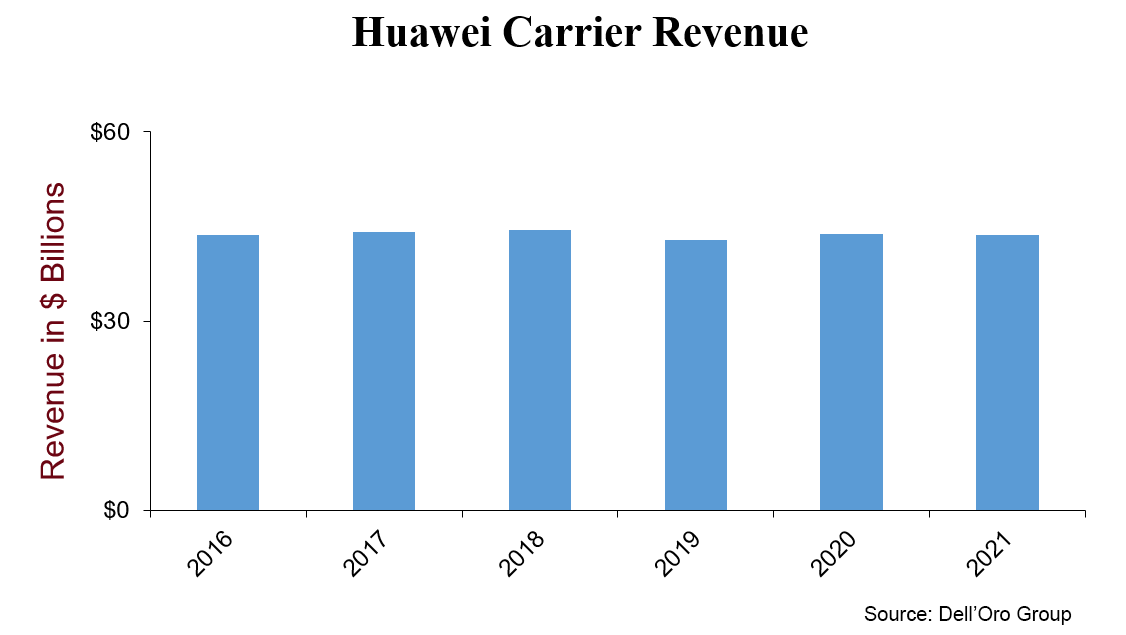
And even as Huawei again reiterated that it has enough components to support its 5G Massive MIMO base stations over the near term, Huawei is expecting the external challenges to intensify in 2022.
In addition to the geopolitical situation, Huawei expressed concerns about Covid-19 restrictions, inflation, forex volatility, trade restrictions, and the overall slowdown in the economy.
The direct and indirect implications from China’s zero-Covid strategy are difficult to quantify. In addition to the softer economy – some economists believe the lockdowns in Shanghai could shave off 2% to 3% from China’s GDP – there is a risk that these policies could exacerbate supply chain issues.
While Huawei’s concerns are valid and important to keep in mind for future output analysis, we also need to recognize that it took the operators six months to a year to adjust capex after the GDP deceleration back in 2001 and 2008/2009.
Huawei also stressed the importance of focusing on the variables within their control, especially when it comes to innovation, maintaining competitive RAN products/services, and supporting the customer.
5G Evolution, 1+1+N = 5.5G
The industry as a whole is moving towards the next phase in the 5G evolution. 3GPP Release 18, also known as 5G-Advanced, is scheduled to become a commercial reality by the 2023/2024 time frame.
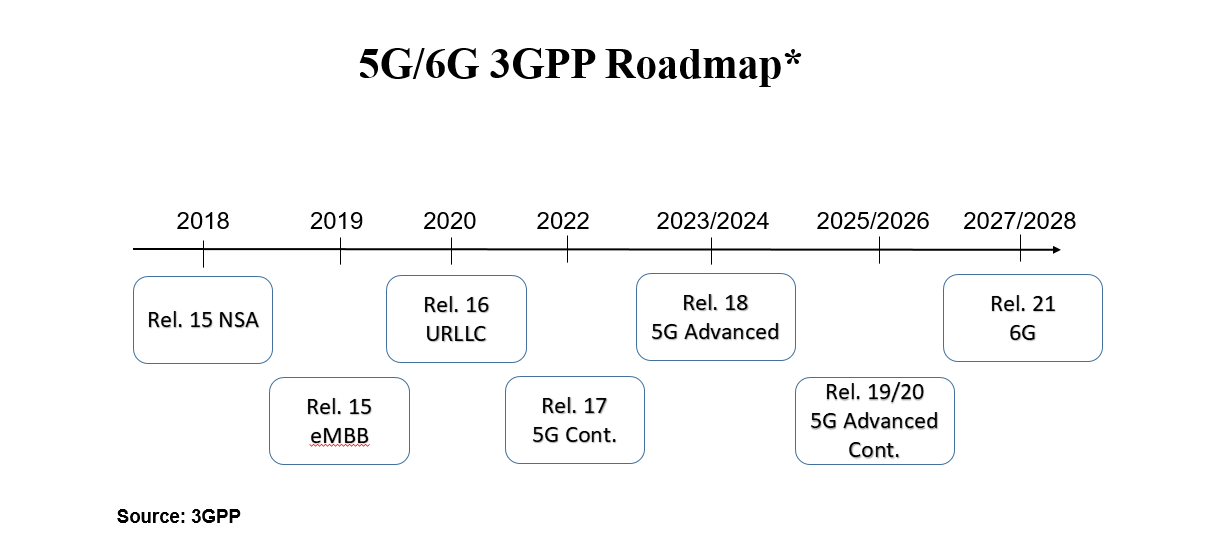
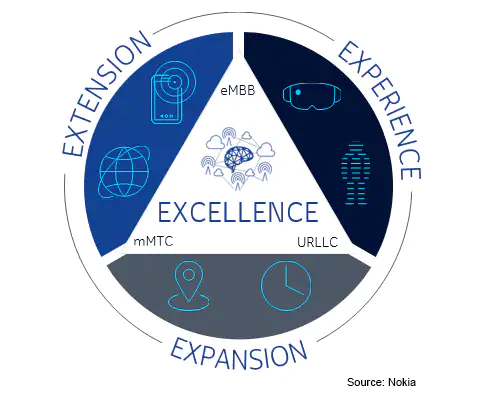
5G-Advanced will take 5G to the next level and create a foundation for more demanding applications and a broader set of use cases. Nokia envisions 5G-Advanced will help to improve the experience, expand the capabilities, extend the reach of connectivity, and spur operational enhancements.
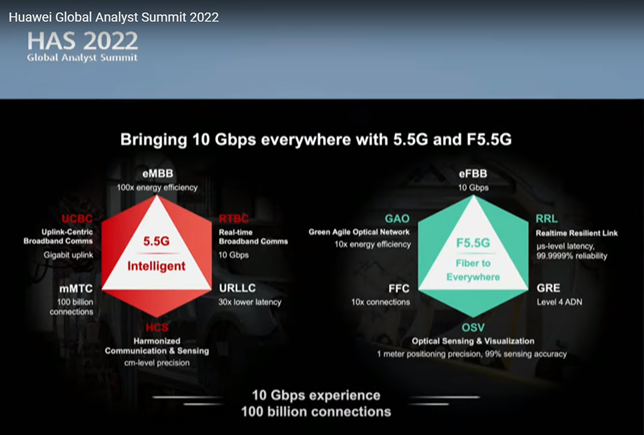
Huawei is marketing the 5G-Advanced evolution as 1+1+N or 5.5G, to reflect the additional layer needed to realize ubiquitous Gbps speeds (current 5G is marketed as 1+N, where 1 represents the foundation network and N refers to the various capabilities and scenarios).
According to Huawei, the 1+1+N (5.5G) architecture is expected to be more commonplace by 2025. It is worth noting here that the Dell’Oro Group does not expect operators will materially grow capex to support the 5.5 G or 5G-Advanced evolution.
B2B
Huawei is engaged in thousands of trials focusing on various 5G private use cases across 20+ verticals such as manufacturing, healthcare, mining, ports, airports, steel production, cement, energy, utilities, and chemistry verticals, to name a few. During HAS 2022, the vendor shared it has installed around 3K 5G base stations to improve the connectivity in 200 coal mines.
And Huawei remains optimistic about the near-term prospects with private 5G. During HAS2022, the vendor implied global 5G B2B small cell growth will approach 100x over the next five years.
Green Sites
Even though the ICT sector only contributes 1.4% (source: Ericsson) of global carbon emissions and 5G sites are projected to drive less than 1% of global electricity consumption (assuming 12 kW per site and 10 M sites), changing the mobile site consumption trajectory is increasingly moving up the priority list for both operators and suppliers.
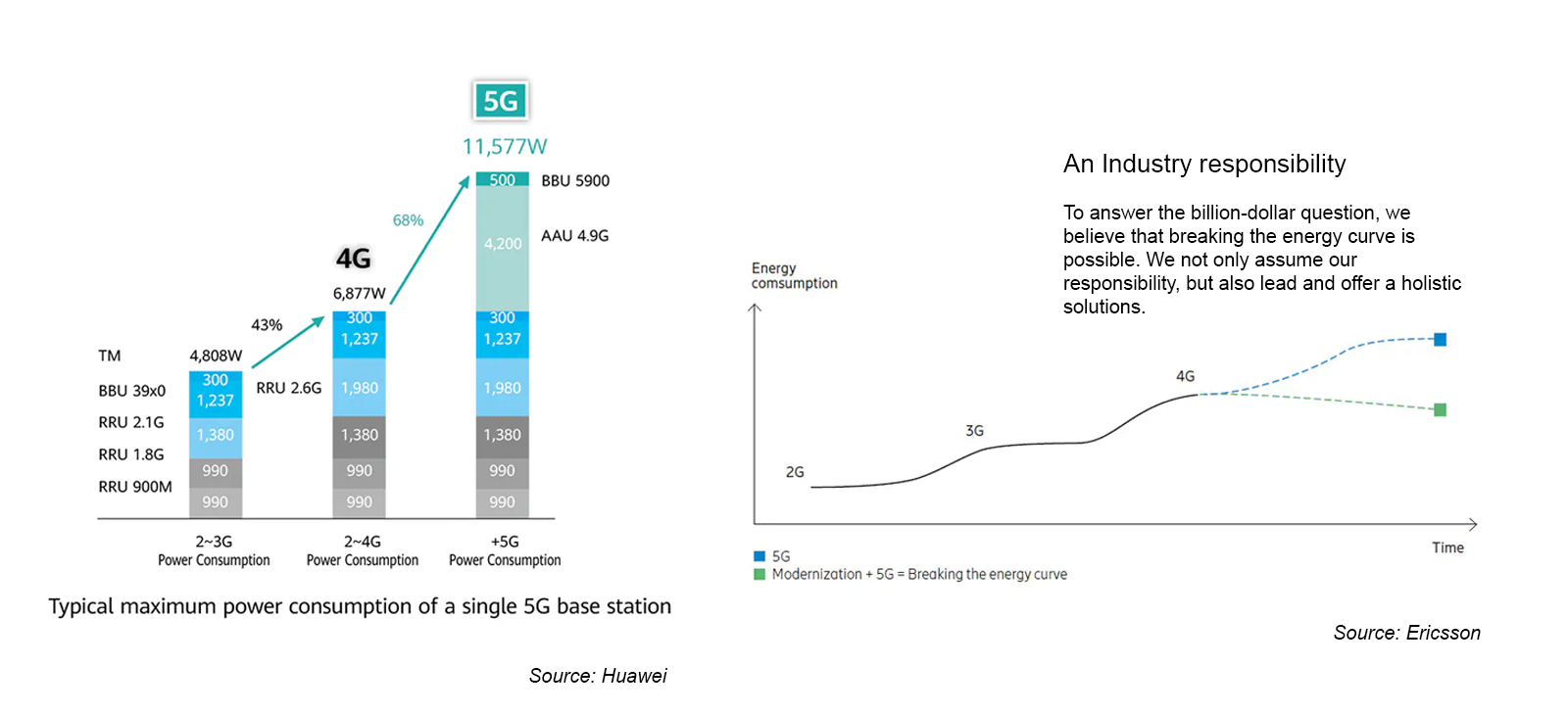
“Green 5G” was an important topic at the HAS 2022 event. Huawei’s latest MetaAAU, RRU, and SDIF antennas are helping to reduce the overall energy consumption. This taken together with more intelligence in the RAN will ideally help to change the overall energy trajectory.
Digital Indoor System (DIS)
The rapid shift from 4G to 5G is not only fueling macro RAN investments. Huawei’s indoor small cell shipments roughly doubled between 2017 and 2021, underpinned by surging 5G DIS deployments. Even with the elevated baseline, Huawei remains optimistic about the long-term growth prospects – buoyed by stable public MBB growth and robust demand for enterprise 5G.
During HAS2022, Huawei reported decent progress with new technologies, including distributed M-MIMO and 5G positioning. Operators in five countries are currently benefitting from the DL and UL throughput boost provided by Distributed M-MIMO.
Despite the challenging geopolitical climate, our estimates suggest Huawei’s was the #1 small cell RAN revenue/shipment vendor in 2021 (Dell’Oro RAN).
Sub 3 GHz
Although upper mid-band WB TDD deployments have dominated the 5G RAN market in this initial phase, sub-3 GHz FDD NR activations are firming up and expected to comprise a greater share of the combined FDD+TTT 5G NR market over the 2021-2026 forecast period.
During HAS2022, Huawei announced multiple enhancements to its NR FDD portfolio in order to better support 4T4R, 8T8R, and Massive MIMO – the latest FDD Massive MIMO product is lighter and smaller, weighing around 47 kg.
In short, some of the key RAN takeaways from Huawei’s 2022 HAS event are consistent with the message that we have communicated for some time, namely that even with the overall RAN growth slowing, it is still early in the broader 5G cycle. There is still some long-term upside with public MBB and material opportunities with private 5G. At the same time, there is no shortage of external challenges to navigate over the near-term.